Meet Lucy®
Hi, I’m Lucy, your AI-powered assistant for enterprise knowledge management. (Nice to meet you!) I help instantly transform terabytes of valuable data into findable answers.
Lucy® is an AI-powered enterprise knowledge management platform.
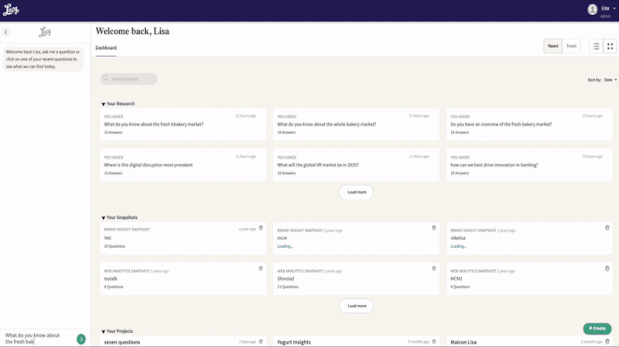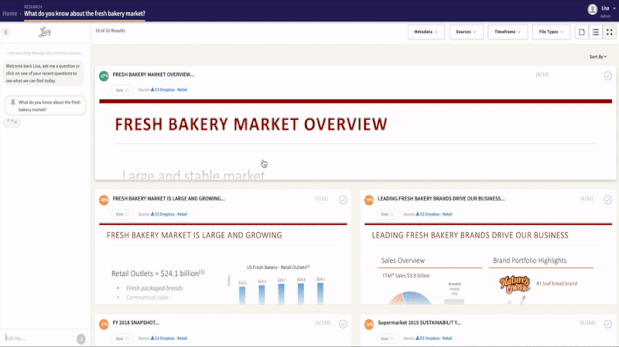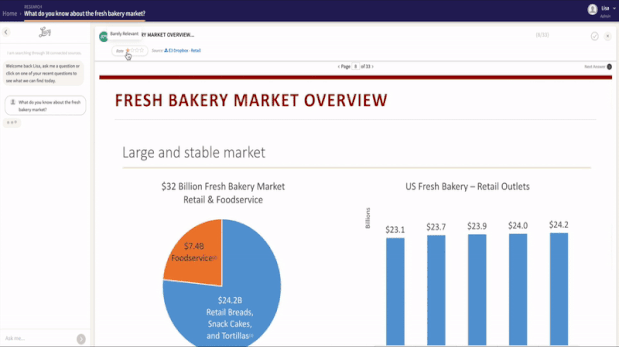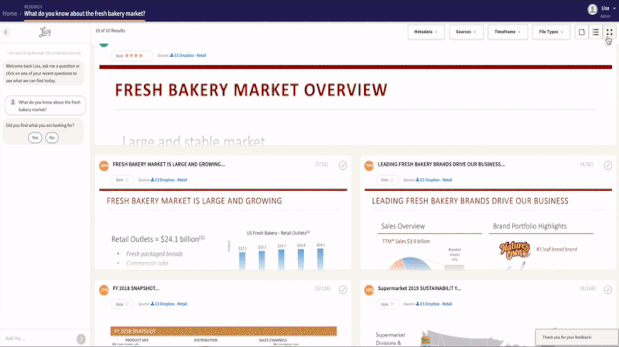
I’ll search your owned and licensed data sources and quickly return the most relevant answers. I’ll show the exact page, chart, paragraph, video clip, or audio byte that answers your question. All your brand’s insights are accessed in one place—a single gateway to your enterprise knowledge.
Lucy® finds the answers where
they live.
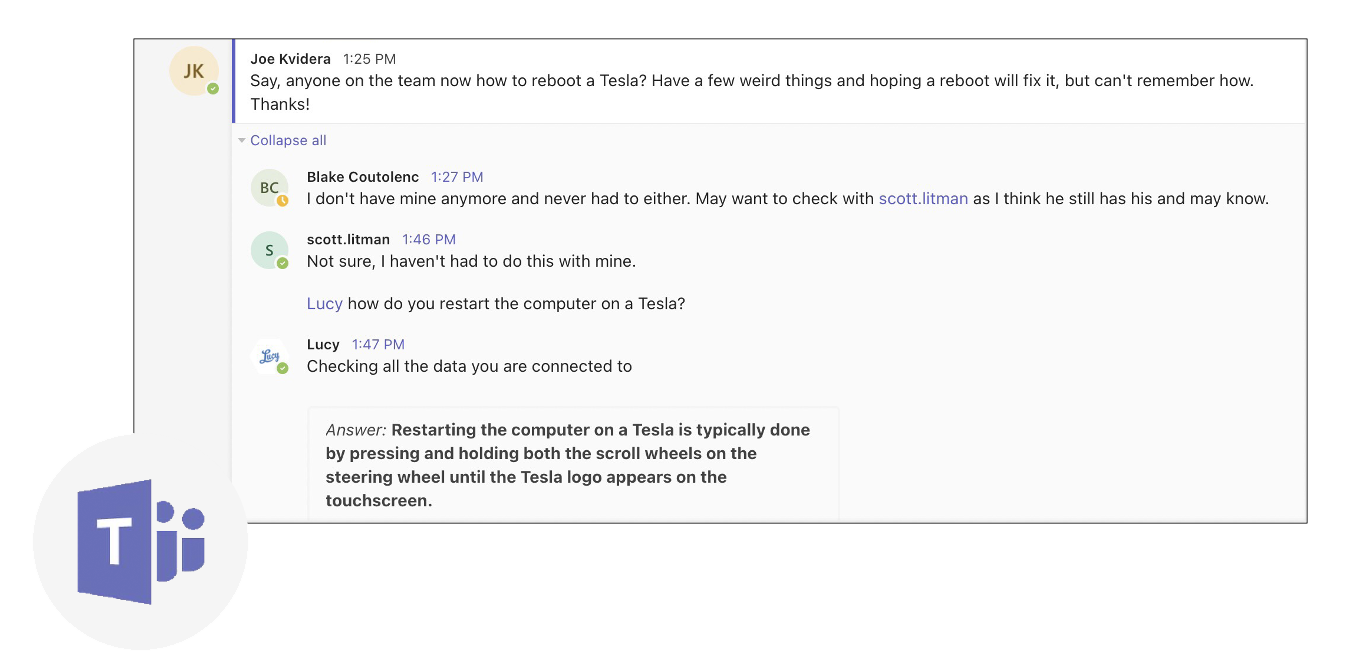
I don’t need your data moved into my system. Through my automated integrations, I learn and remember all of the data stored across your internal files and systems. I can even connect to many popular third party subscriptions. When I answer your question, you will know just where I found it.
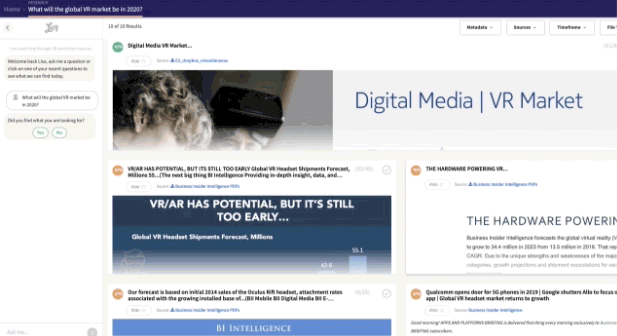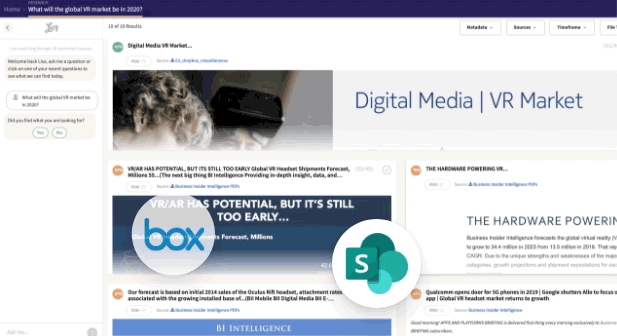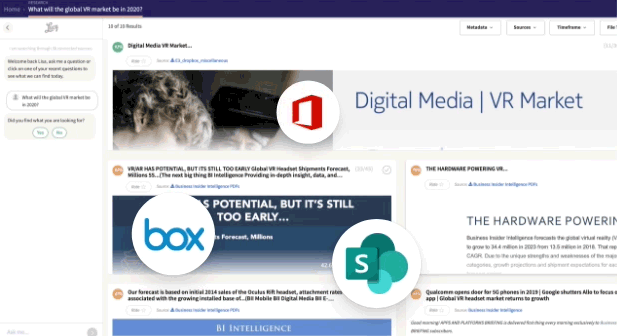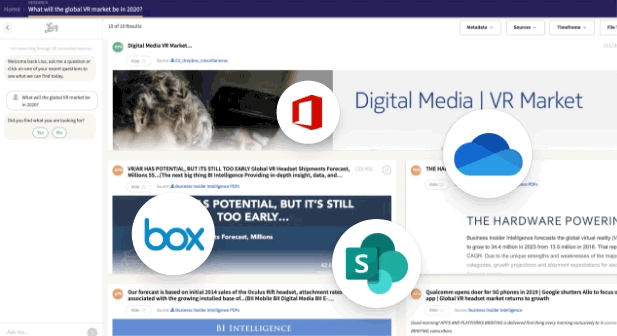
Lucy® uses metadata and
document search.
I automatically generate multilevel, filterable metadata, so there’s no need for humans to spend time manually tagging files. I can also locate documents based on chosen criteria, like document source, author, or publish date. I deliver focused answers from relevant content in record time, giving you a truly different way to search.
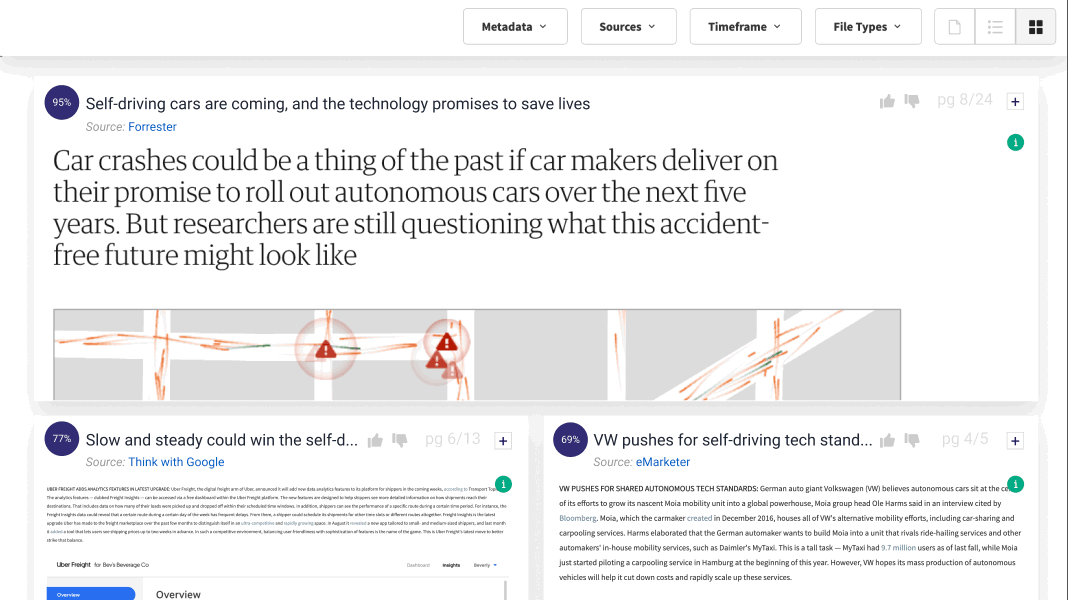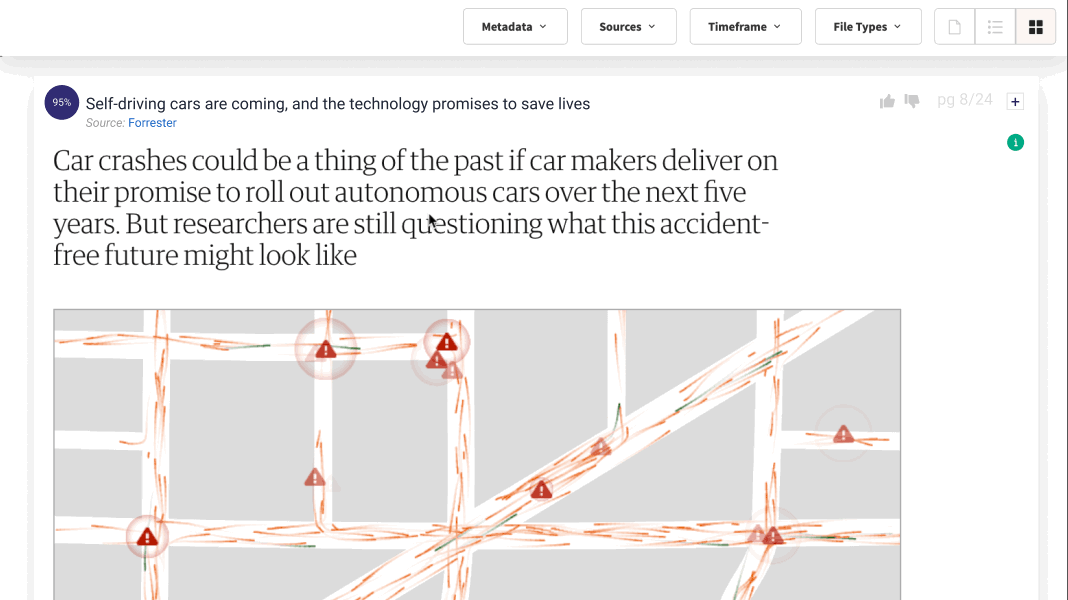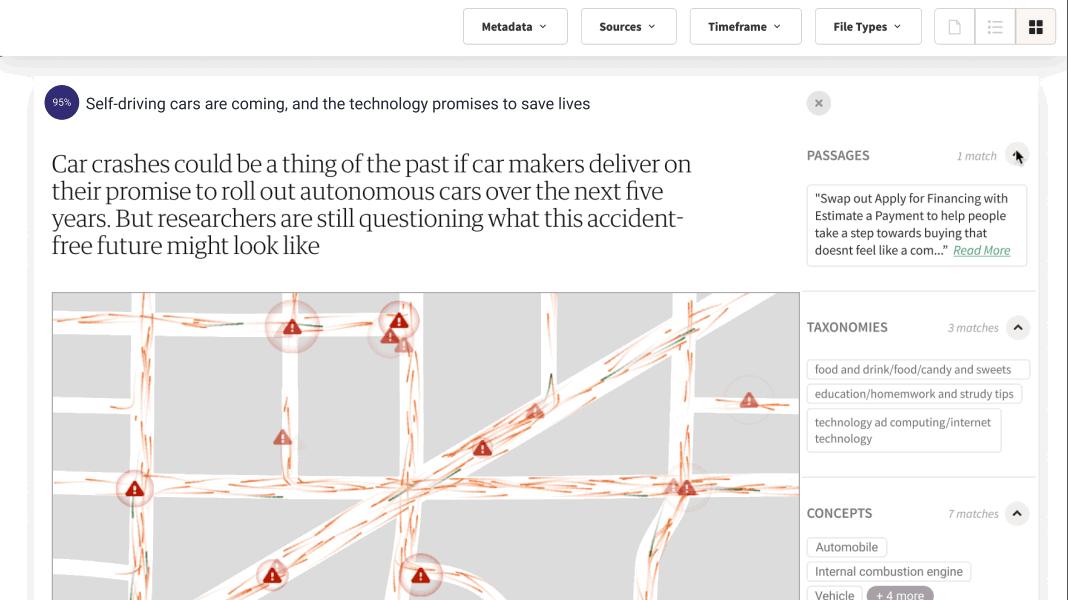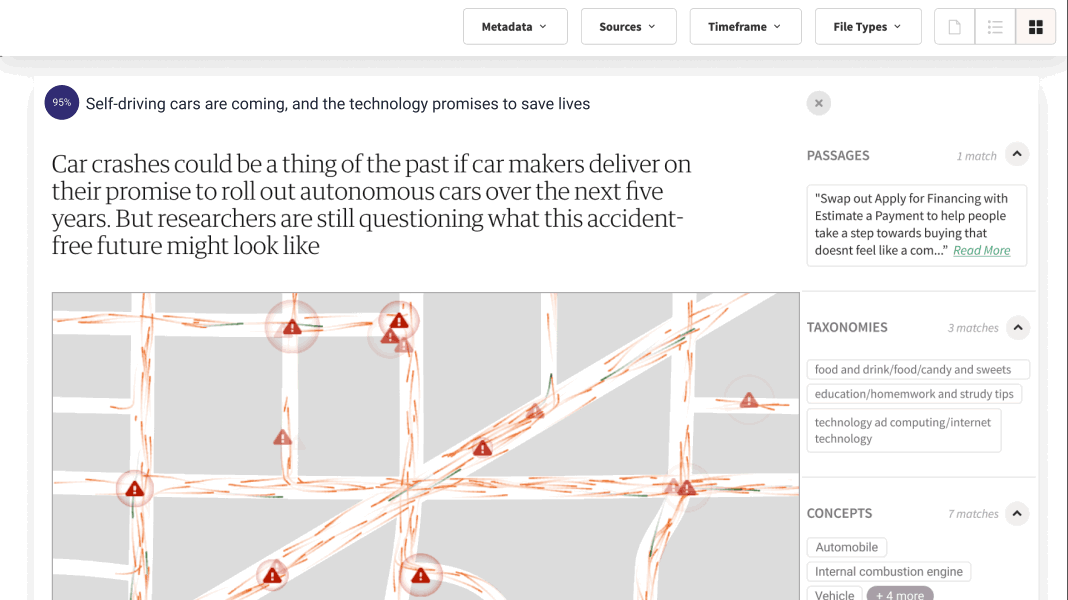
Lucy® is always learning.
Through machine learning, I continuously learn and improve as you give me feedback. If for some reason I’m not giving you the best answer available within your data, you can use Lucy Assist and my dedicated support team will be put on the job to help us out.
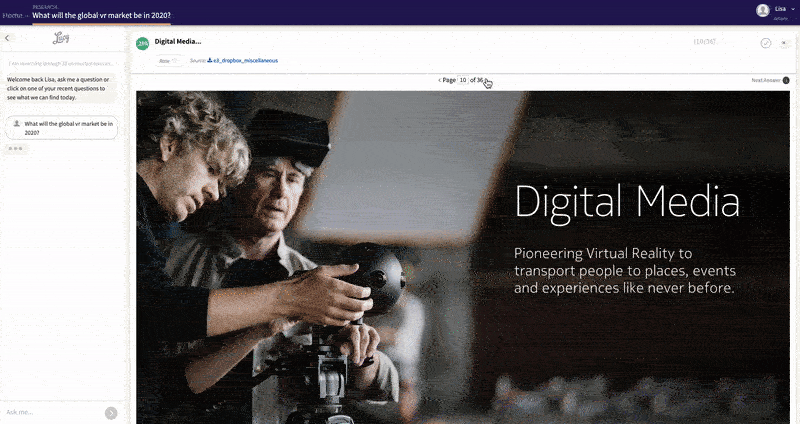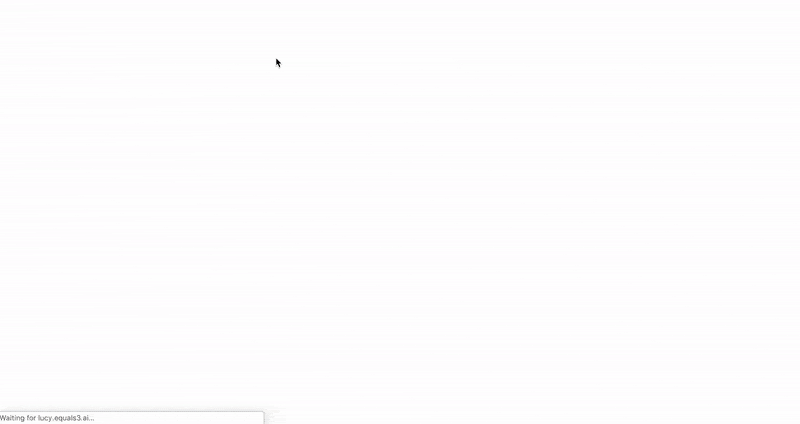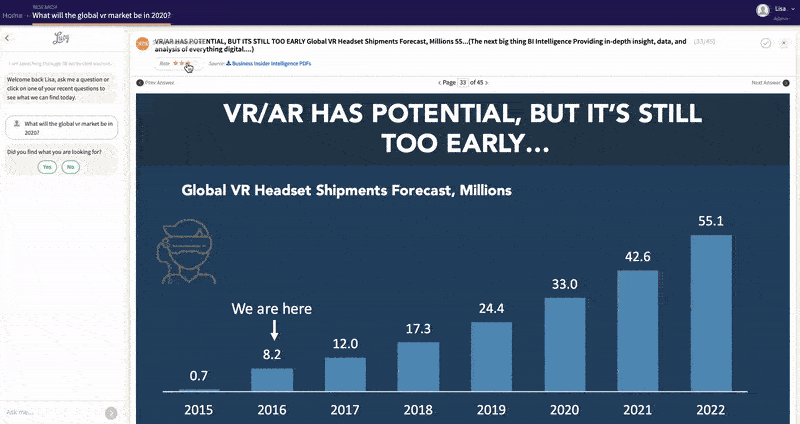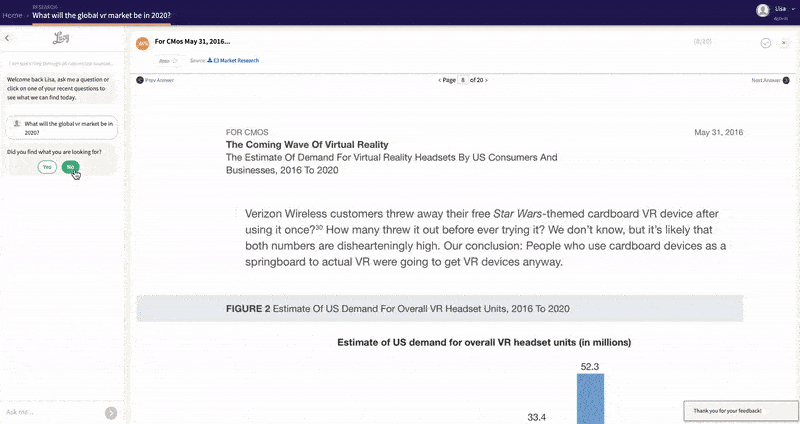
Learn More about Lucy®
That was just a quick overview of what I can do for you, but there’s so much more to cover. If you want to learn more about me, complete the form below to get in touch with my creators. We look forward to hearing from you!